CDD Research & Development
Research Topics, Methodologies & Facilities
● Countering cyberattacks against AI/ML (e.g. Model Extraction, Bias Introduction, Reflexive Adaptation & Data Repudiation [RADaR])
● Advanced machine augmented learning architectures (e.g. SqP/SyP) that are resistent to cyberattack
● Neuromorphic computation applied to the cyber security arena
● Applied Machine Learning - Hybrid cybersecurity for blended attacks
● Augmented Identification and Authentication - Similarity heuristics and hylomorphic analytics
● Alternative Quantum data structures supportive of Quantum Machine Learning (QML)
● Enhanced, blended cybersecurity modeling using formal frameworks
(E.g. NIST CSF - ISO27K - NCSC-CAF)
● Commercial Quantum Readiness Programme
● Methodology Interoperation (e.g.CDD[CMM]/NIST-CSF/MITREAtt&ck)
● Strict and full PRINCE-II Development Disciplines (Internal to CDD)
See supportive Recent Reading below:
The CDD R&D arena includes:
Development
- General Development - XTools, Swift, C & C++, Python, Jupyter
- High Performance Parallelism and Multi-processing - Python / OpenCL etc for GPU-architectures
- High Speed Demand (Assembler) - NASM / YASM / CUDA
Research
- Augmented Human Congition ('Generative AI') - KERAS, TensorFlow, PYTorch(Tensors/Transformers/LLM/Datamining), Scikit-Learn, MATLAB, Numpy, (+ Bitarray(large) GIMP_ML Open-CV etc.)
- Digital Twin Technology for the Security Arena) - to mitigate unpredictable, undesirable emergent behavior in complex cyber security environs.
- Quantum Computation - CIRQ, IBM Qiskit, TensorFlow-Quantum

CDD Operational Facilities
● Dedicated, Secure Premises & Telephony
● Secure (Govt.Approved) Storage
● PRINCE2 Development Processes (46 combinatorial Instruments in PASCAL & PEDDLE )
● Integrated BAU Operational Administration
● Forensic Analytics Practice
● Advanced IT Development Facilities
● Developmental Supercomputing Architecture (+ internal Advanced Developmental Programme)
● Green Power (and Uninterrupted Power Supply)
● Web Presence, (including secure WAN/LAN, VPN and secure cloud domain)
● Technical Reference Resources (Electronic/Physical Library + Bodleian Access)
● PI/PL Insurance / Professional Memberships
● Training Programme
CDD Operational Environ (dedicated entirely to supporting our research)
Combinatorial/Operational Summary:
Full Integration of 114 Cores & 960GB RAM / 20TB Storage / 40GBit N/W / Combined 31.8GHz - ZMM-[512bit] + Xeon throughput providing advanced, ultra-high performance GP-GPU (processing across large matrices (tot. 33GB) with + Metal-3 and support augmented CUDA) combined on:
- AMD Radeon Pro 5500M - Intel UHD Graphics 630 - AMD Radeon ProVega 64X
High Throughput Machine Space:
Apple Servers: MacPro-128GB, iMacPro-128GB and MacMini-64GB
Development and Analytics:
Apple MacBook Pro, iMacPro, MacPro (+Sonoma)
Design and Research:
iMac and iPad Pro
Software Arena:
[ SPECIALIST TECHNICAL ARENA/MATERIAL REDACTED ]
All Technical Documentation - LaTeX
Innovation - Brain Tech - Notability - ProCreate
Development - SWIFT Pycharm
Network Analytics - WireShark
CDD Cyber Security Transmutative Systems Development
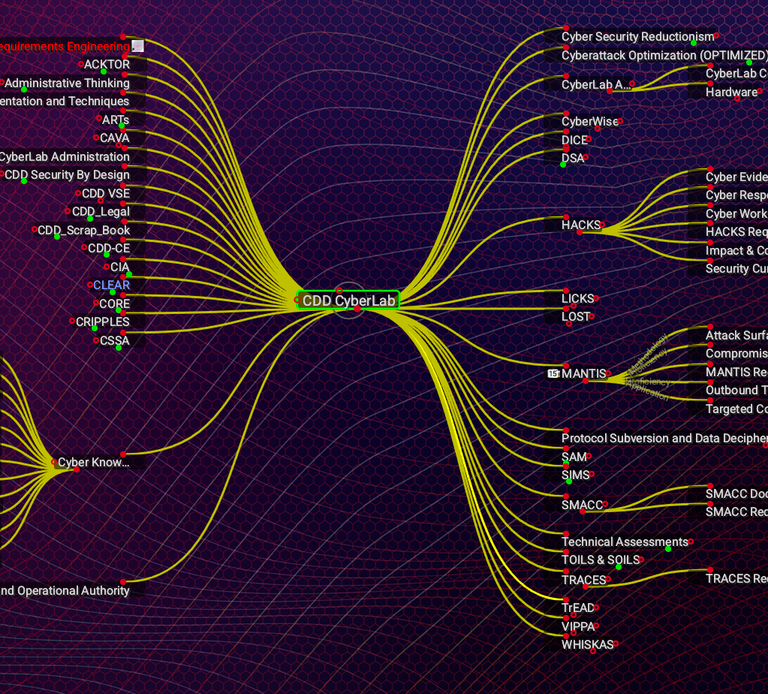
CDD has progressed development in a number of areas of cyber security which call upon techniques from expert systems, neural networks, machine learning, deep neural networks and augmented human cognition (that some confuse with AI). A modest portfolio of sub-systems are available to consultants in the performance of specialist security services. Some organisations have adopted similar techniques in bespoke engineering scenarios.
CAVA - Cyber Audit and Verification Arena
CORE - Cyber Operational Response Engineering
CSA - CyberSec Situational Awareness
SAM - Security Assurance Metrication
DSA - Dynamic Security Assessment
SIMS - Security Information Mapping System
WHISKAS - REDACTED
OILS - Operational Intelligence and Logistics System
SMACC - REDACTED
MANTIS - REDACTED
CCAS - Cyber Conflict Analytics System
ARTTS - Advanced Response Techniques to Threatened Systems
VIPPA - REDACTED
VASE - Vulnerability Analytics Search Engine
CIA - REDACTED
CsMM - Cybersecurity Maturity Methodology
LICKS - Logical Intelligence Control for Knowledge-based System(s)
TrEAD - Trust Engineering, Architecture and Deployment
CLEAR - Correlated Log Engineering for Advanced Reconnaissance.
ACTOR - Advanced Crypto-key Transmission for Operational Resilience
FRBSA - An advanced Facial Recognition Biometric Security Architecture
CDD Patent Preparation/Submissions
SqP/SyP/SmP Data Structure
Final Preparation for Submission (2024)
NNGL
Short Peer Review and Preparation(2023)
DMAD&R
In Preparation for Submission (2024)
CDD Recent Reading (for research guidance and commentary)
A question is repeatedly arising for CDD, namely how firms and individuals might get involed with machine learning architectures.
A really good start has been provided by a Dr. Jason Browlee...a very experienced proponent of machine learning (and AI if you like such terminology), and this document provides some excellent guidance on how to approach the subject. There is a very large corpus of material in the CDD technical library and this can be made available to anyone making a reasonable request and whom might benefit from such access. (Please make contact).
How CDD goes about preparing high-throughput hyper-parallel processing architectures using GPUs.
Details the instruction set and the microcode formats native to this family of processors that are accessible to programmers and compilers. The main purposes of this document are to specify the language constructs and behavior, including the organization of each type of instruction in both text syntax and binary format. Also it provide a reference of instruction operation that compiler writers can use to maximize performance of the general purpose AMD processor.
NAT Interim Incident Report
Learning to learn with Quantum Neural Networks via classical neural networks
Finding good parametrisation characteristics for QNN, rapidly identifying approximate optima in the parametr landscape (QAOA for MaxCut and QAOA for Sherrington-Kirkpatrick Ising model and Variational Quantum Eignesolver for the Hubbard model), reduction in the number of optimization iterations, optimization strategies learned by the NN generalsing well across a number of problem instance sizes and training on small problem instances in oder to initialise larger, intractable simulations on quantum devices. LINK
Universal quantum control through deep reinforcement learning
Control optimization of reinforcement learning techniques using DNN.
TensorFlow Quantum: A software framework for quantum machine learning
The introduction of TFQ for high level abstractions for the design and training of both generative and discriminitive quantum infomration models for simulation of high performance quantum circuits.
Assessment of Deployed Cryptographic Policy in Government/Military Operational Sphere
In relation to the three areas of special interest, the following specific cryptographic policy areas deployed for Military Alliance and Government by CDD include:
800-186 Recommendations for Discrete Logarithm-based Cryptography: Elliptic Curve Domain Parameters
800-175B Rev. 1 Guideline for Using Cryptographic Standards in the Federal Government: Cryptographic Mechanisms
800-175A Guideline for Using Cryptographic Standards in the Federal Government: Directives, Mandates and Policies
800-152 A Profile for U.S. Federal Cryptographic Key Management Systems (CKMS)
800-140F Rev. 1 CMVP Approved Non-Invasive Attack Mitigation Test Metrics: CMVP Validation Authority Updates to ISO/IEC 24759
800-140F CMVP Approved Non-Invasive Attack Mitigation Test Metrics: CMVP Validation Authority Updates to ISO/IEC 24759
800-140E CMVP Approved Authentication Mechanisms: CMVP Validation Authority Requirements for ISO/IEC 19790 Annex E and ISO/IEC 24579 Section 6.17
800-140D Rev. 2 Cryptographic Module Validation Program (CMVP)-Approved Sensitive Security Parameter Generation and Establishment Methods: CMVP Validation Authority Updates to ISO/IEC 24759
800-140C Rev. 2 Cryptographic Module Validation Program (CMVP)-Approved Security Functions: CMVP Validation Authority Updates to ISO/IEC 24759
800-140B Rev. 1 CMVP Security Policy Requirements: CMVP Validation Authority Updates to ISO/IEC 24759 and ISO/IEC 19790 Annex B
800-140B CMVP Security Policy Requirements: CMVP Validation Authority Updates to ISO/IEC 24759 and ISO/IEC 19790 Annex B
800-140A CMVP Documentation Requirements: CMVP Validation Authority Updates to ISO/IEC 24759
800-140 FIPS 140-3 Derived Test Requirements (DTR): CMVP Validation Authority Updates to ISO/IEC 24759
800-135 Rev. 1 Recommendation for Existing Application-Specific Key Derivation Functions
800-133 Rev. 2 Recommendation for Cryptographic Key Generation
800-131A Rev. 2 Transitioning the Use of Cryptographic Algorithms and Key Lengths
800-130 A Framework for Designing Cryptographic Key Management Systems
800-57 Part 3 Rev. 1 Recommendation for Key Management, Part 3: Application-Specific Key Management Guidance
800-57 Part 2 Rev. 1 Recommendation for Key Management: Part 2 – Best Practices for Key Management Organizations
800-57 Part 1 Rev. 5 Recommendation for Key Management: Part 1 – General
800-56C Rev. 2 Recommendation for Key-Derivation Methods in Key-Establishment Schemes
800-56B Rev. 2 Recommendation for Pair-Wise Key-Establishment Using Integer Factorization Cryptography
800-56A Rev. 3 Recommendation for Pair-Wise Key-Establishment Schemes Using Discrete Logarithm Cryptography
All rights reserved. CyberDefenceDynamics
© 2013-2024
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details and accept the service to view the translations.