Essential IT Security [ contact: Cyber Dynamics IT Professionals ]
These services provided by CDD build upon any existing foundational IT security, (or indeed, new IT facilities) geared to the following groups:
Small Businessess or Subsidiaries
Smaller corporate entities with IT facilities that may be sub-par and require security systems enhancement that addresses a percieved change in threat profile.
Private Individuals
With Important IT
People with significant IT skills, but find themselves needing greater assurance that their security is commensurate with the threat.
Troubled
Organisations
Organisations finding themselves temporarily facing significant threat activity that requires more capability than their personnel can currently call upon.
People Facing Significant IT Difficulty
People who may lack the necessary capability to take control of an IT related problem and require guidance to resolve matters or champion their cause.
Entry-level Policy-led Cybercapability Improvement
All entities that use the internet in any way, will be benefiting from IT security in some form. It is some times necessary to take control of such security mechanisms, and user communities will be advised accordingly.
The following temporary services are desirnged to help users and organisational entities to benefit from taking greater control of their IT security.

Threat, Vectors, Vulnerability & Risk
The relationship between these four is often misundertstood, but it is crtiical to know where risk lies, and how this can be meaningfully expressed in terms of threat, vector and vulnerability, otherwise money may be wasted or good businesses can be completely lost! In the context of the impact of cyberattack:
- Risk is a mathematical probability and can be mitigated
- Threat(s) are most frequently people and such entity's actions are resisted appropriately
- Vectors are the routes by which vulnerability might be exploited
- Vulnerabilities are inherent weaknesses in systems and these need mollification.
CDD will meaningfully clarify for customers, where cyberrisk arises and how best to mitigate such risk most cost effectively.

Cyber Situational Awareness
It is critical to know (with as much certainty as possible) what is transpiring within an IT arena. If you cannot see what is happening, then the IT is being driven blind and all may be lost if a cyber incident takes place. This involves:
- Identifying sources of operational intelligence
- Gathering And Correlating All Such Sources
- Interrogating And Discerning Issues Arising
- Establishing Event Prioritisation
CDD can asssit in preparation of the above technical processes to ensure that organisations become aware of the natural performance of their IT arena and are able to exert the necessary management influence over that arena. Technical improvements to system log collection and correlation plus basic threat analysis and hunting, vector, vulnerability and impact analysis.
Risk Reduction
Risk is omnipresent and equally, can always be reduced, dependent upon risk apetite. Accepting needless risk is frequently considered unwise. Assessing and managing IT risk usually involves the 4Ts for business processes or more properly:
- Toleration
- Treatment
- Transferral
- Termination
CDD asserts that there may be a fifth option, (Transmutation) but only for those with the capabilities described in the section on Advanced Cybersecurity Services and even then, only by those with a full understanding of the Art of Cybersecurity. CDD can advise and prepare assurance mechanisms underpinning risk management to make sure that attention is directed to appropriate areas of cyberrisk.
Cyber Security Response
Following appropriate diagnosis and timeline of a cyber attack, it is critical to understand what options are available and what influence can be called into play including:
- Legal Advice And Even Police Involvement
- Communications Planning & Orchestration
- Cyber Insurance Policy
- Forensic Capability
- Technical Recovery
- Alternative Process Invocation
- Other Temporary Restorative Operational Measures
CDD can prepare or advise on all such measures and approaches.

Cyber Security Incident Review
Following recovery from the adverse impact of a cyber incident it is critical to assess what can be improved to better equip the organisastion for the next event. Such forensic review may call upon many areas of business continuity and recovery including:
- Time Line Analysis
- Decision Taking (and possible mistakes)
- Critical Information Requirements
- Legal Implications
- Cyber Insurance Claim (Progression)
- Process Review
- Skills-set Review
CDD can take control of, or prepare or advise on all such forensics, interdiction and/or intercession.

Cyber Security Performance
Security enforcing functionality has increasing cost, and it is essential that addressing cyber risk can be justified. Preparing appropriate cogent argument around such investment is critical. To take such decisions, it is necessary to prepare meaningful cost/benefit metrics encompassing:
- Impact
- Risk
- Maintenance
- Training
- Service
CDD can prepare or advise on all such performance metrics to guide decision makers accordingly.
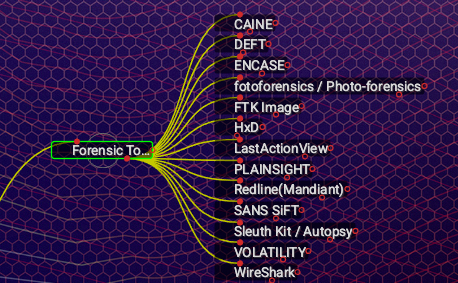
Forensic Practices
CDD deploys a range of forensic tools and capability most appropriate to achieve the desired goal of the client including:
- Time Line Analytics
- Disk Drive and USB Analytics & Recovery
- Hash Filtering & P/W Hash Access/Recovery
- File System Analytics
- AI Faked Photos & Video Footage (by metadata clone/error/noise)
- Keyword Search, Memory Dumps
- Mobile & N/W Traffic Capture & Forensics
- File System Analytics & Metadata Data Access
- Device Driver Activity & Running Process Analytics
- Last Actions, Internet History and Event Log Analysis
CDD Security Policy (By National Institute of Science & Technology) In Relation To Entry Level Cyber Security
800-137 Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations
800-137A Assessing Information Security Continuous Monitoring (ISCM) Programs: Developing an ISCM Program Assessment
800-86 Guide to Integrating Forensic Techniques into Incident Response
800-83 R.1 Guide to Malware Incident Prevention and Handling for Desktops and Laptops
800-82 R.3 Guide to Operational Technology (OT) Security
800-82 R.2 Guide to Industrial Control Systems (ICS) Security
800-61 R.2 Computer Security Incident Handling Guide
800-55 R.2 Performance Measurement Guide for Information Security
800-55 R.1 Performance Measurement Guide for Information Security
800-53 R.5 Security and Privacy Controls for Information Systems and Organizations
800-53B Control Baselines for Information Systems and Organizations
800-53A R.5 Assessing Security and Privacy Controls in Information Systems and Organizations
800-50 Building an Information Technology Security Awareness and Training Program
800-97: Wireless Network Security: 802.11, Bluetooth, and Handheld Devices
800-41 R.1 Guidelines on Firewalls and Firewall Policy
800-35 Guide to Selecting Information Technology
800-34 R.1 Contingency Planning Guide for Federal Information Systems
800-30 R.1 Guide for Conducting Risk Assessments
All rights reserved. CyberDefenceDynamics
© 2013-2024
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details and accept the service to view the translations.
